ICICI Bank's Twitter based service is poorly thought through because it really does not require two-factor authentication, as the bank claims. icicibankpay is not at all "Safe & Secure". It is easily prone to being highjacked on both the sender's and receiver's sides. Another issue is that there is nothing customers can do to opt-out or block this service. It therefore puts all ICICI bank customers at risk of fraud.
The service works as follows: to sign up, an ICICI bank customer chooses to follow the bank's account (handle) on Twitter, and the bank's handle then automatically follows the customer. The customer must then send a private message (direct message or DM) to the bank's handle on Twitter with the customer's registered mobile number. The bank then sends the customer a verification code via SMS on that mobile number. Finally, the customer must send the code back to the bank via Twitter direct message.
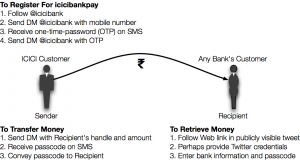
To send money, the customer must send a direct message to ICICI bank containing the recipient's Twitter handle and the amount. The bank then sends a 4-digit passcode via SMS to the sender and a Tweet to the recipient with a link to ICICI bank's Web site. The sender must tell the recipient the passcode, and by following the tweeted link, the recipient can authenticate her Twitter account, enter her bank details and the passcode. ICICI transfers the funds to her account.
Since ICICI sends an SMS code to the registered mobile number, it claims that it is following 2-factor authentication safeguards. However, ANY Twitter user can follow the bank and send the registration message. Therefore, the code sent by SMS is in fact the only form of authentication. If a bank customer loses his mobile phone and it falls into a wrongdoer's hands, the customer's ICICI account is primed for theft
Cyber security expert Vikas Bhatia of Kalki Consulting agrees with this risk assessment. "My biggest concern is the sign up process through Twitter," he wrote via email from New York. When ICICI's service was brought to the attention of Pranesh Prakash, who deals with privacy and information security issues at the Centre for Internet and Society in Bangalore, he responded in a tweet:
The entire process of registering and sending money can take far less than five minutes, so it is possible that money can be stolen well before the customer can report the loss of the phone and get the number deactivated.
While the fraud scenario described above would be isolated to a single customer at a time (but should still never be allowed to exist), there are other ways that the system is vulnerable to a larger scale attack that might defraud thousands of users at a time.
It could happen like this: When one Twitter handle follows another, that event is available for anyone on Twitter to see in real time. Since mostly bank customers would follow ICICI's account, this narrows the pool of potential targets for any criminals, and they can concentrate on targeting these users. By using other publicly availably information to exploit the user, the customers' computers or phones could be infested with malware. Once the criminals have amassed enough potential victims, they can strike.
Bhatia wrote, "The risk I see is that the user hasn’t actively signed up for the service and their account is taken over. The prevalent use of open source based smartphones, primarily Android, means that homemade malicious apps could intercept the SMS messages intended to authenticate the account holder."
There are very clear vulnerabilities that can be exploited on the recipient end as well. Say someone who was the recipient of a transfer via this service left their computer unattended for a few minutes. If the person was already logged in to Twitter, then they will not be asked to re-authenticate when they follow the link in the tweet from the bank. Furthermore if they left their phone at the computer or they use an app that syncs up messages on the phone with the computer, then once again there is only one authentication, and a third party could enter any other bank account details.
Bhatia summed up with, "This service could be used as a mechanism to launder money used to fund terrorism and organized crime. It appears that even though both the sender and recipient need phones, twitter accounts and bank accounts these requirements could be understood and exploited by criminals."
ICICI's saving grace may be that not that many people have signed up for the service and the rate of inscription is fairly slow. With a Rs10,000 daily limit on transfers, if a fraud attack took place any time soon, the payoff would be small. However, if the bank manages to sign up a few hundred thousand users and enough of their accounts/devices were compromised, an attack would net a few million dollars at least.
ICICI was alerted to security issues through Twitter and LinkedIn messaging, but as of now nobody from the bank has responded. The RBI was also contacted through its Web site but has not responded.
Get updates from NewsPie and support us by liking our page on Facebook. What did you think of this article? We welcome your comments below.
Sushil Kambampati is a digital media expert and the founder of NewsPie. Follow him on Twitter






I don’t know, whether you know about two factor authentication or not. If not, let me describe you:
1: What User Know : This is being followed here because user can’t use the service without logging in to twitter account. That is where first factor is tested itself.
2: What User Own : This is being followed through OTP in this particular case.
The scenario, which you are explaining is like : “Hey fraudester, I have opened the door of my house, and the key of almirah is already there and the safe vault is open. So please go ahaed and do whataever you want”. If an user is using Twitter or in that case any application for banking purpose, the primary guideline which comes is to logout from the app. Smartphone is a personal device, which is intended to be used for personal use and keep locked using pin or pattern. The kind of scenario, which you are describing is easily replicable in case of Apple TouchID too, where user is authenticated using the third factor(Who User Is), beacuse the phone can be unlocked using any of the registered finger print and then the logged in user can go use phone. But that is not what smartphone meant for, These are personal devices, the app running in them (FB, Twitter etc) do not only contain a financial risk but greater reputational risk too. User’s, who are using them are well aware of these security features i.e. locking the phone, logging out from app. It seems you aren’t.